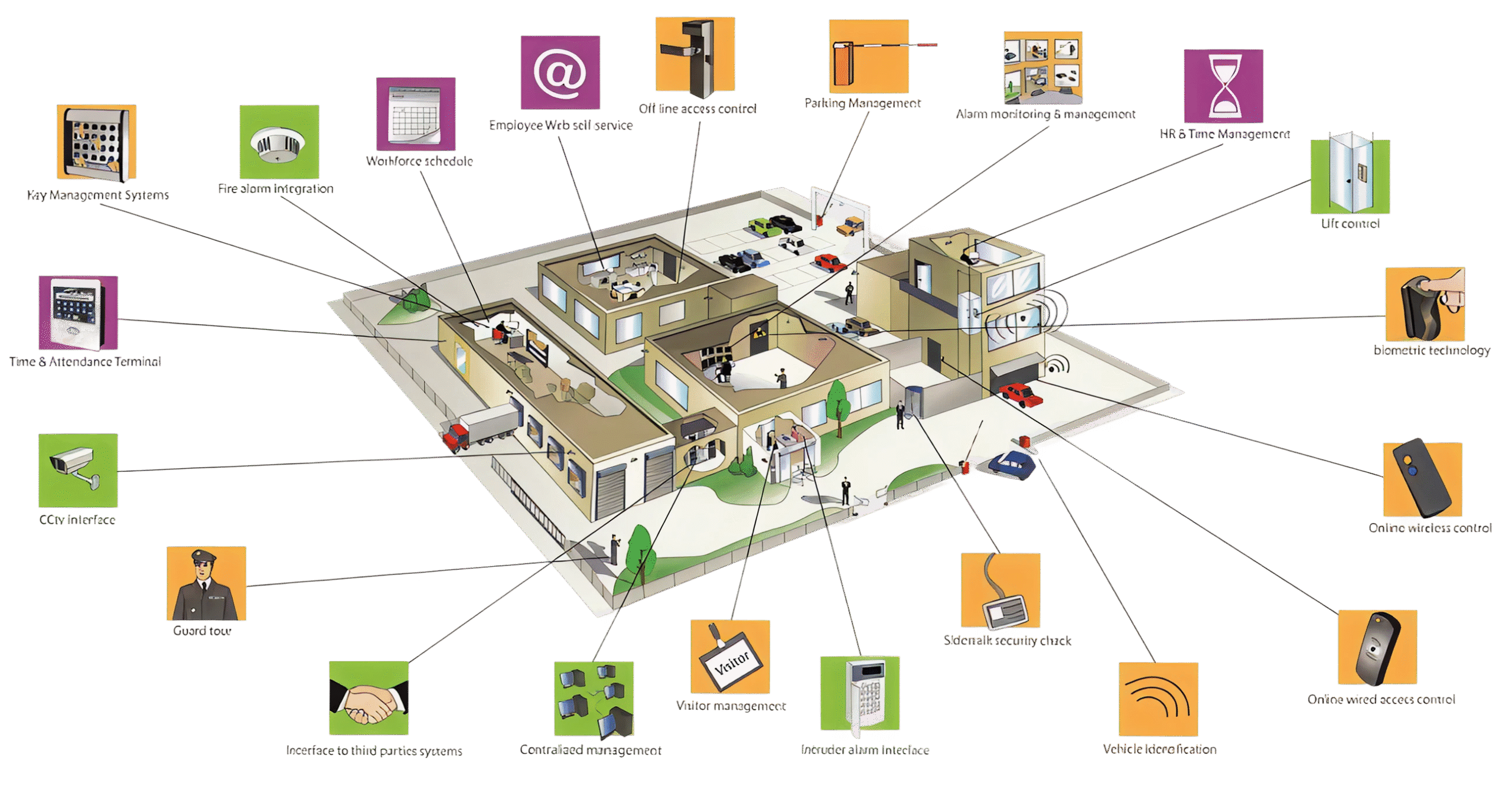
Integrated Security Solutions
Integrated security solutions provide a unified approach to managing and mitigating the growing complexity of physical and cyber threats. Modern organizations face challenges ranging from cyberattacks and physical intrusions to data privacy concerns and regulatory compliance. Traditional, siloed (separated) security systems are inadequate for handling today’s multi-faceted threat landscape. This summary outlines the benefits, components, and practical implementation of integrated security solutions.
Why Unified Security Is Essential
- Evolving Threat Landscape: Threats now cross over multiple domains (physical and digital), making isolated security measures ineffective.
Siloed System - Limitations: Operating different security tools independently leads to blind spots, slow response times, and inefficient operations.
- Integrated Approach: By connecting all aspects of security, organizations gain enhanced visibility, situational awareness, and the agility to address sophisticated attacks.
What Are Integrated Security Solutions?
Integrated security solutions combine various security disciplines—such as physical access control, video surveillance, and cybersecurity—into a single, coherent system. These solutions leverage advanced technologies like artificial intelligence (AI), machine learning (ML), and automation to:
- Provide a real-time, holistic (complete) view of an organization’s security status.
- Enable swift and accurate detection of threats across all domains.
Key Principles of Integrated Security
Advanced Access Control
Manages and monitors entry/exit points using biometrics, smart cards, and remote management.
Intelligent Video Surveillance
Uses high-definition cameras, AI analytics (like facial recognition, object tracking), and real-time alerting.
Comprehensive Cybersecurity
Defends network infrastructure, detects cyberthreats, and responds to incidents.
Centralized Management
Controls all security functions via a single dashboard for instant insights and proactive response.
Benefits of Integration
Cost Reduction
Consolidates systems and reduces the expenses of managing multiple vendors and outdated hardware
Faster & More Accurate Threat Response
Correlates data from different systems for quicker identification and mitigation of risks
Operational Efficiency
Streamlines management through automation and unified dashboards
Stronger Compliance
Enforces consistent security policies to help meet regulatory demands
Enhanced Situational Awareness
Security teams gain a comprehensive view to make quick, informed decisions
Real-World Example: Global Logistics Security Overhaul
A multinational logistics company resolved fragmented security by:
- Integrating physical access, surveillance, and cybersecurity on one platform
- Upgrading systems and providing staff training
- Achieving uniform security protocols, faster incident response, and improved oversight
Why Choose This Solution?
Comprehensive Integration
Covers physical, cyber, and operational security in one system
Expert Support & Proven Success
Offers end-to-end guidance from planning to maintenance
Scalable, Future-Proof Technology
Utilizes AI/ML for adapting to evolving threats and organizational growth
Next Steps & Resources
- Consultation Available: Personalized security assessments to tailor solutions
- Resource Hub: Access whitepapers, expert advice, and latest security trends on the provider’s website
Conclusion
Cybersecurity is a business imperative, not just an IT concern. A proactive, layered approach—combining technical solutions, policy, employee awareness, and ongoing adaptation to threats—is essential for effective protection.
Key Jargon Explained:
- Malware: Malicious software designed to harm or infiltrate systems.
- Phishing: Attempts to trick individuals into revealing confidential information.
- Encryption: Encoding data so only authorized people can read it.
- Multi-Factor Authentication (MFA): Requiring multiple proofs of identity.
- SIEM: Systems that collect and analyze security information and events.
- Zero Trust: Security model where no entity is trusted by default.
- IoT (Internet of Things): Everyday devices connected to the internet (e.g., smart thermostats).
- GDPR, CCPA, HIPAA: Major laws/regulations governing data privacy and protection.
Ready to get started?
Contact us today, to learn more about our Integrated Security Solutions, and how we can help take your business to the next level. Let us handle your IT, so you can focus on what matters cost – driving your business forward
Related Articles
This presentation offers an in-depth overview of modern security system solutions, detailing core technologies, their integration, benefits, and strategic implementation for...
ferbetech
•
28 July 2025
Biometric access control systems are growing in popularity over other access control systems that use access codes, key fobs or access...
ferbetech
•
28 July 2025
Sunter Park Apartment is a modern residential complex located in North Jakarta, designed to accommodate urban living with high security standards...
ferbetech
•
2 July 2025
PT Pupuk Kujang was established on June 9, 1975, with a total capital of US$ 260 million — comprising a loan...